~ Cheat Engine Basics Tutorial(Step 1 - 7) ~ (прохождение туториала CE)
Ссылка на оригинал статьи
Yo! I noticed that many people ask for help in CE tutorial. So I decided to explain it here. I will not explain only to pass it but to learn some basics. Do not use password just to pass step you can’t do, that's useless. You won't learn and gain anything...
If someone will make topic “Help on 3rd step of tutorial!!” or anything like that, direct him to this one, unless mine is not explained clearly/he do not understand what I wrote.
If you will see that something is not right or something is not clearly explained, PM me and I will edit it.
This tutorial contains 7 steps. You can jump to anyone you want when you will enter password in 1st step window in right bottom corner. Ok, here we go:
FIRST OF ALL, open Cheat Engine. If it will ask you to open tutorial, click yes. If u already clicked no, go to cheat engine folder and find it there. Once you opened tutorial, we can start...
(Texts wrote in "code", with darker background are default step descriptions, below them there is mine)
Step1 - Introduction
Code:
Welcome to the Cheat Engine Tutorial. (v2.5)
This tutorial will try to explain the basics of cheating on games, and getting you more familiar with Cheat Engine.
First open Cheat Engine if it hasn't been opened yet.
Then click on the 'open process' icon. (top left icon, with the computer on it)
When the process window is open find this tutorial. The process name is probably 'tutorial.exe' unless you renamed
me.
Select it, and click ok. Just ignore all the other buttons right now, but experiment with them later if you feel like it.
When everything went right, the process window should be gone now and at the top of CE the processname is
shown.
Now, click NEXT to continue to the next step. (Or fill in the password to proceed to that particular step you want)
First open Cheat Engine and Tutorial. Now, click the button with computer icon on it (It’s in top left corner). New window will pop up. Here, you can choose proccess that you want cheat with. Find Tutorial.exe proccess, click on it and click Ok button, or just double click on this proccess. If you done everything right, proccess name you chose(Tutorial.exe) should be written in top of Cheat Engine window. If it does, click next.
Step 2 - Exact Value scanning (Password: 090453)
Code:
Now that you have opened the tutorial with Cheat Engine lets get on with the next step.
You see at the bottom of this window the text Health: xxx
Each time you click 'Hit me' your health gets decreased.
To get to the next step you have to find this value and change it to 1000
To find the value there are different ways, but I'll tell you about the easiest, 'Exact Value':
First make sure value type is set to at least 2 bytes or 4 bytes, 1 byte will also work, but you'll run into a
(easy to fix) problem when you've found the address and want to change it. The 8-byte may perhaps works if the
bytes
after the address are 0, but I wouldn't take the bet.
Single, double, and the other scans just dont work, because they store the value in a different way.
When the value type is set correctly, make sure the scantype is set to 'Exact Value'
Then fill in the number your health is in the value box. And click 'First Scan'
After a while (if you have a extremly slow pc) the scan is done and the results are shown in the list on the
left(if
the number of addresses it found are less than the number below that list)
If you find more than 1 address and you dont know for sure wich address it is, click 'Hit me', fill in the new
health
value into the value box, and click 'Next Scan'
repeat this untill you're sure you've found it. (that includes that there's only 1 address in the list.....)
Now double click the address in the list on the left. This makes the address pop-up in the list at the bottom,
showing you the current value.
Double click the value, (or select it and press enter), and change the value to 1000.
If everything went ok the next button should become enabled, and you're ready for the next step.
Note:
If you did anything wrong while scanning, click "New Scan" and repeat the scanning again.
Also, try playing arround with the value and click 'hit me'
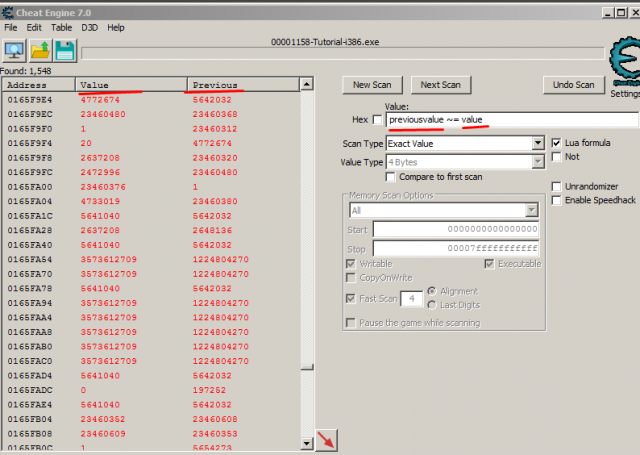
In this step you have to find health value and change it to 1000.You will learn here how use Exact Value Scanning and for what is it. Let’s say that you play some game, and with each hit we lose some HP(health). Now force enemy to hit you(click “Hit me” button below your health). As you can see, your health decreased. Now go to Cheat Engine, in Scan Type choose Exact Value, in Value Type choose 4 Bytes, type number of your health in window above Scan Type and click First Scan(If you already have scanned before, cause you were curious or you wanted to click this button, you will have New Scan instead of First Scan. Click it and then do what I just said). Below computer icon(this one in top left corner) you can see “Found:”. It shows you how many addresses with value matching to one you wrote were found. If there are too many(“too many” are when addresses are not displayed in window below “found:”, in CE v5.3 there is probably no limit for displayed addresses...), click New Scan and get hurt once again(by clicking on “Hit me” in tutorial window). Type in CE new HP value and click First Scan. Do it until some addresses will be displayed in window below “found:”. Of course there are more ways to find correct value, but this tutorial heading is “Exact Value Scanning”, so we will use only this option.
Ok when you have displayed few addresses, go to tutorial (Leave CE as it is, with these addresses in the list) and click “Hit me”. Go to CE, look on found addresses list and find decreased value(previously every address was equal to number of health before this hit. So when previously your health were 96, look for value smaller than this one, but at once it have to be equal to new health number). Example: I had 96HP, and after that hit I lost 5, so now I have 91. So I have to look for 91 value, while almost every other will be 96. So our will differ from others, which makes it easy to find.
Once we found it, click on it and press red arrow pointing to left/down, or just double click on it. It will show in window on bottom of CE. There you can see 5 labels: Freeze(If it’s ticked, value of address in same line will be froze/stopped, it will not be able to change), Description(as it says, you can add it by yourself), Address(shows address), Value Type(Shows type of value stored in address in same line), Value(shows value stored in address in same line). Our objective is to change HP value to 1000, so double click on value. New window will open with current amount of value. Change it to 1000 and click OK. If everything went ok, you should be able to click Next in tutorial window to go to next step. If you can’t that means that you changed value to wrong one, or you changed wrong value(you have wrong address).
So if you made something wrong here’s one more time everything what above, but in shorter version:
- In tutorial click hit me
- In cheat engine write number of your health and click first scan
- If you got too many addresses, press new scan, then hit me and write new amount of HP. Repeat it until you will find only few addresses(about 20-30 or less).
- If you found enough few, go to tutorial and click hit me
- Go to cheat engine, look on list of addresses on left and look there for address equal to new amount of HP(it’s easy to find it cause it differ from others)
- If you found it, double click on it. It will move to window on bottom
- Now double click its value(It is in vertical line under Value label). New window will show
- Write here 1000 and click OK
- Go to tutorial and click Next
Step 3 – Unknown Initial Value (Password: 419482)
Code:
Ok, seeing that you've figured out how to find a value using exact value let's move on to the next step.
In the previous test we knew the initial value so we could do a exact value, but now we have a statusbar where
we dont know the starting value.
We only know that the value is between 0 and 500. And each time you click 'hit me' you lose some health. The
ammount you lose each time is shown above the statusbar.
Again there are several different ways to find the value. (like doing a decreased value by... scan), but I'll only
explain the easiest. "Unknown initial value", and decreased value.
Because you dont know the value it is right now, a exact value wont do any good, so choose as scantype
'Unknown initial value', again, the value type is 4-bytes. (most windows apps use 4-bytes)
click first scan and wait till it's done.
When it is done click 'hit me'. You'll lose some of your health. (the ammount you lost shows for a few seconds and
then disapears, but you dont need that)
Now go to Cheat Engine, and choose 'Decreased Value' and click 'Next Scan'
When that scan is done, click hit me again, and repeat the above till you only find a few.
We know the value is between 0 and 500, so pick the one that is most likely the address we need, and add it to
the list.
Now change the health to 5000, to proceed to the next step.
Ok here you have to find value stored in bar and cahgne it to 5000. Same as previous, but here we do not have exact value… but bar! What could be stored in it ? One thing is sure – value from 0 to 500. It would take way too long to search for every value using exact value scan type. So here we have to look for “Unknown Initial Value”. In Scan Type choose it and click first scan. It should find a lot of addresses(it finds ALL adresses that store 4 bytes values, unless you choose other value type). So to reducethis amount a little, we have two options:
-
Easier(for beginners) – After first scan click “Hit me” in tutorial, go to cheat engine and, chagne Scan Type to Decreased value(you know why, cause we will look for decreaed values, and one of them is our helath) and click Next Scan. It should find few addresses. Our address is 0 – 500, so look for similar one. If you found more than one, and you aren’t sure which one is it, you can click “Hit me” and check which one decreased, or click “Hit me” and scan for Decreased Value once more. Your choice.
-
Faster(You have to remember decreased value if you want to use this one) - After first scan click “Hit me” in tutorial, go to cheat engine and, chagne Scan Type to Decreased value by… and write here amount of lost HP(if you clicked “Hit me” more times, you have to sum up every decreased amount ) and click Next Scan(example: I clicked Hit me and I lost 5hp, so I write 5). It should find only 1, at least ONLY few values.
Ok now we have value stored in bar, change it to 5000(if you got to this step by yourself, I assume that you can do it). After that, click Next in tutorial window to go to 4th step.
Step 4 – Floating Points (Password: 890124)
Code:
In the previous tutorial we used bytes to scan, but some games store information in so called 'floating point' notations.
(propably to prevent simple memory scanners from finding it the easy way)
a floating point is a value with some digits behind the point. (like 5.12 or 11321.1)
Below you see your health and ammo. Both are stored as Floating point notations, but health is stored as a float and
ammo is stored as a double.
Click on hit me to lose some health, and on shoot to decrease your ammo with 0.5
You have to set BOTH values to 5000 or higher to proceed.
Exact value scan will work fine here, but you may want to experiment with other types too.
Hint: It is recommended to disable "Fast Scan" for type float.
Here we have to find value for HP and ammo and change them to 5000 or higher. Do it same as previous, but instead of 4 bytes Value Type look for Float(if you scan for HP) or Double(if you scan for ammo). If you need explanation, here it is:
Change Value Type to Float, Scan Type to Exact Value and look for [amount of HP]. Use exact value with floats and doubles ONLY if value you look for do not have numbers behind dot(91.56). If it has, use some other options like Value Between… and write here… you know what. If somehow you don’t know, here is example(I have 56.81321384321964 HP, so I will write in Value Between… 56 and 57, or 56.8 and 56.9 for more precise scanning). Of course you can use others if you want.
Once you found HP value, double click on it to add it to bottom list(let’s call this list Cheat List). Now do the same but change scan type to Double and look for ammo(you can use Values Between too if you want).
If you will find both addresses, change their values to 5000 or higher, go to tutorial and click Next.
Step 5 – Code Finder (Password: 888899)
Code:
Sometimes the location something is stored at changes when you restart the game, or even while you're playing.. In
that case you can use 2 things to still make a table that
works.
In this step I'll try to descibe how to use the Code Finder function.
The value down here will be at a different location each time you start the tutorial, so a normal entry in the address
list wouldn't work.
First try to find the address. (you've got to this point so I assume you know how to)
When you've found the address, right-click the address in Cheat Engine and choose "Find out what writes to this
address". A window will pop up with an empty list.
Then click on the Change value button in this tutorial, and go back to Cheat Engine. If evrything went right there
should be an address with assembler code there now.
Click it and choose the replace option to replace it with code that does nothing. That will also add the code address
to the code list in the advanced options window. (Wich gets saved if you save your table)
Click on stop, so the game will start running normal again, and close to close the window.
Now, click on Change value, and if everything went right the Next button should become clickable.
Note: When you're freezing the address with a high enough speed it may happen that next becomes visible anyhow
Ok scan for value that is in tutorial. If you got this far by yourself, you have to be able to find it. Once you found correct one, add it to Cheat List. Now right click on it and choose “Find out what writes to this address”. Confirmation window will pop up, click YES. Now you can see empty window with some unclickable buttons. Ok go to tutorial and click Change Value. Return to blank window. Some strange line of letters will appear in it. Click on it once and then press Replace(button to the right). Choose any name you want, you won’t need it now and click OK. Click Stop and then Close to return to Cheat Engine main window. Ok I’m explaining what you just did:
You replaced code that was responsible for changing value with nothing, so now Change Value button in tutorial window will NOT work. Want to see? Go ahead to tutorial and click Change value. See? Once you did it, Next button should be available. Click it to proceed to 6th step.
Step 6 – Pointers (Password: 098712)
Code:
In the previous step I explained how to use the Code finder to handle changing locations. But that method alone
makes it difficult to find the address to set the values you want.
Thats why there are pointers:
At the bottom you'll find 2 buttons. One will change the value, and the other changes the value AND the location of
the value.
For this step you dont really need to know assembler, but it helps a lot if you do.
First find the address of the value. When you've found it use the function to find out what writes to that address.
Change the value again, and a item will show in the list. Double click that item. (or select and click on more info) and
a new window will open with detailed information on what happened when the instruction ran.
If the assembler instruction doesnt have anything between a '[' and ']' then use another item in the list.
If it does it will say what it think will be the value of the pointer you need.
Go back to the main cheat engine window (you can keep this extra info window open if you want, but if you close it,
remember what is between the [ and ] ) and do a 4 byte scan in hexadecimal for the value the extra info told you.
When done scanning it may return 1 or a few hundred addresses. Most of the time the address you need will be the
smallest one. Now click on manually add and select the pointer checkbox.
The window will change and allows you to type in the address of a pointer and a offset.
Fill in as address the address you just found.
If the assembler instruction has a calculation (e.g: [esi+12]) at the end then type the value in thats at the end. else
leave it 0. If it was a more complicated instruction look at the calculation.
example of a more complicated instruction:
[EAX*2+EDX+00000310] eax=4C and edx=00801234.
In this case EDX would be the value the pointer has, and EAX2+00000310 the offset, so the offset you'd fill in
would be 24C+00000310=3A8. (this is all in hex, use cal.exe from windows in scientific mode to calculate)
Back to the tutorial, click OK and the address will be added, If all went right the address will show P->xxxxxxx, with
xxxxxxx being the address of the value you found. If thats not right, you've done something wrong.
Now, change the value using the pointer you added in 5000 and freeze it. Then click Change pointer, and if all went
right the next button will become visible.
extra:
In this tutorial the value is actually pointed to by a pointer to a pointer, but to finish this tutorial only 1 pointer will be
needed. To find the pointer to this pointer, just search for what changes the value of the pointer.
If you know assembler, you may see something like
mov eax,[ebp-4]
mov eax,[eax+310]
Dont be confused by this. just use the value the extra info window tells you. ebp-4 points to the stack which
contained the pointer to this pointer, but the stack location does change all the time, so dont search for ebp, search
for the value of eax
Pointers are wonderful. They posses great power. They are very useful. Like I said, VERY useful. Pointer is like arrow/line/finger that points specific address’s value. It will point it always, even if value will change its location. Most games now uses values changing addresses, so pointers are really important.
First, scan for value shown on the bottom of tutorial window. If you will find it, find out what writes to it, go to tutorial and change value. Now return to window that appeared after clicking “find out what writes to this address”. There should be some code. Click on it and select “More information” or just double click it. See code with red arrows on its left? If it points to code that’s between [ and ], look what is written under “The value of the pointer needed to find this address is probably” and Remember it. Now go to CE main window, and tick “Hex” box near window where you write value that you want to scan for. If you ticked it, in window next to this box should appear 00000000. Change it with remembered value and click First Scan. It should find one/few addresses. Now, look at left and down. You will see “Add address manually” button. Press it. New window should pop up. In it, tick “Pointer” box. After this, window should get longer. In Address of pointer write address(Address, no value! Address is this one on left, under “Address” label)which you found when you were scanning for hex value. In Offset (hex) write 0(yea, just zero). Click OK. In bottom window you should see new address, like P->xxxxxxxx, and next to it its value. If value is ??, you made something wrong. Here is shorter version for this, if you failed:
- Find value(this one in tutorial window)
- Find out what writes to it
- Change value and double click on just shown code in “Find out what…” window
- Remember what is written under ” The value of the pointer needed to find this address is probably”
- In Cheat engine tick “Hex” box(it’s under New Scan/First Scan)
- Write remembered code and scan for it
- If it found 1 address, remember it. If it found few, correct one is probably this one at the top. NOTE. Remember Address, no value! This is important!
- Click “Add address manually” button
- Tick “Pointer” box
- In Address of pointer write remembered address
- In Offset(Hex) leave 0
- Click Ok
- in bottom window look on new address(it should be P->xxxxxxxx)
- If its value is ??, repeat step from 1-14
Go to tutorial window and click Change Pointer. Now you have 3 seconds to change our pointer(address with P->xxxxxxxx) to 5000. Don’t worry if you missed. Just once more click Change Pointer and once more try to change it in time. If you will, click Next.
Step 7 - Code Injection: (Password: 013370)
Code:
Code injection is a technique where one injects a piece of code into the target process, and then reroute the
execution of code to go through your own written code
In this tutorial you'll have a health value and a button that will decrease your health with 1 each time you click it.
Your task is to use code injection to increase the value of your health with 2 every time it is clicked
Start with finding the address and then find what writes to it.
then when you've found the code that decreases it browse to that address in the disassembler, and open the auto
assembler window (ctrl+a)
There click on template and then code injection, and give it the address that decreases health (If it isn't already filled
in correctly)
That'll generate a basic auto assembler injection framework you can use for your code.
Notice the alloc, that'll allocate a block of memory for your code cave, in the past, in the pre windows 2000 systems,
people had to find code caves in the memory(regiosn of memory unusaed by the game), but thats luckely a thing f
the past since windows 2000, and will these days cause errors when trying to be used, due to SP2 of XP and the NX
bit of new CPU's
Also notice the line newmem: and originalcode: and the text "Place your code here"
As you guessed it, write your code here that will increase the health with 2.
a usefull assembnler instruction in this case is the "ADD instruction"
here are a few examples:
"ADD [00901234],9" to increase the address at 00901234 with 9
"ADD [ESP+4],9" to increase the address pointed to by ESP+4 with 9
In this case, you'll have to use the same thing between the brackets as the original code has that decreases your
health
Notice:
It is recommended to delete the line that decreases your health from the original code section, else you'll have to
increase your health with 3 (you increase with 3, the original code decreases with 1, so the end result is increase
with 2), which might become confusing. But it's all up to you and your programming.
Notice 2:
In some games the original code can exist out of multiple instructions, and sometimes, not always, it might happen
that a code at another place jumps into your jump instruction end will then cause unknown behaviour. If that
happens, you should usually look near that instruction and see the jumps and fix it, or perhaps even choose to use a
different address to do the code injection from. As long as you're able to figure out the address to change from inside
your injected code.
Ok now you are in 7th step, you can’t call yourself n00b anymore(If you got here by yourself). So, code injection, as it says, is when you inject code/piece of code into the process. Like in this tutorial, we have HP and it decrease by 1 every time you click “Hit me”. We have to inject our code to change Hit me button operation. It has to increase(yea, increase, never heard about Hit me increasing health…) HP by 2 every time we will click it. So let’s do it.
Find that value and find out what writes to that address. Then decrease HP(by clicking Hit me). In “find out what…” window some code will appear. It’s responsible for HP decrement by 1. Click it and then press “Show Disassembler”. Big window with 3 sub windows will appear. At the top of upper left window you will see code that decrease HP by 1. Click it to see its comment(Comment is shown between top and bottom window, in this narrow bar).
It should be “Decrement by 1”. Ok that was unnecessary. Now go to tools -> Auto Assemble, or just click Ctrl + A. White window will pop up, in which click Template -> Code Injection. Write here address of health decrement(It should be already filled in with correct code. To ensure, write there address with “Decrement by 1” comment). Some assembler strings will appear. It’s <basic auto assembler injection framework you can use for your code>. Whatever it is, I call it template. Now, you see “// Place your code here” under “newmem”(every phrase in assembler started with “//” is comment and they are not entertain when compiling/writing code). According to tutorial, you have to write your code there, but there are 3 options(I have no idea what assembler rules are or whatever, so I have no idea if there is any difference between these options. If someone know and there IS difference, PM me and i will eventally change it).
Important!: Remember, that “Your code” is this one wrote in Memory Viewer after second dash in line where is your address(this address with “Decrement by 1” comment). We call it "your code" but realy it's just code that we want to cheat/change/inject into it code.
By the way: I gathered some info about few assembler instructions by myself, for now I haven’t asked anyone if it’s true, but I will write it here:
- “inc” instruction increases address’s value by 1(I can’t set it to increase more, I don’t even know if it’s possible)
- “dec” instruction decreases address’s value by 1(See: what is above in brackets)
- “add” instruction adds to address’s value, value that is after the code, after coma.
Ok back to tutorial. 3 options: (Remember that [aaa+xxxxxxxx] is our code, I hope you know what our code is, if you do not, once more read starting with “Important!”)
-
Like it’s in tutorial, write your code(with “[aaa+xxxxxxxx]” format) in place of “// Place your code here” comment, and at the beginning of this code place “add“(with space between “add” and code). Now, after this code, write “,3”(“coma three”, no spaces. In total it should look like this: “add [aaa+xxxxxxxx],3 ). Do you know why 3(we want to increase value by 2, not 3!)? Because few lines under newmem there is orginalcode, which decrease this value by 1. Our code increase by 3, so in total(decrease by 1 and increase by 3) these codes increase value by 2.
-
If you don't want that orginalcode to decrease our value(so we could write 2 after code under newmem, not 3), delete "orginalcode:" and "label(orgianlcode)"(this label is in third line from top). Now, change value after your code(under newmem) from 3 to 2, because there is no orginalcode now, which was decreasing our value by 1. I hope you understand.
-
I made some mistake in third option, i will edit it in minute...
Now if you done one of written options, click “Write Code” button at the bottom of Auto Assemble window. If it shows some error, unfortunately you have to repeat. If it shows confirmation window, click OK. Now every time you will click Hit me in tutorial window, your HP should increase by 2. If they does, that’s mean that you made everything correct and Next button will be clickable. Click it to go to last step in Cheat Engine 5.3.
If they doesn't... well... reapeating it would be boring and useless, so i created 3 ready codes for every option:
- Version according to tutorial:
Code:
alloc(newmem,2048)
label(returnhere)
label(originalcode)
label(exit)
00455D7F:
jmp newmem
nop
returnhere:
newmem:
add [ebx+0000030c],3
originalcode:
dec [ebx+0000030c]
exit:
jmp returnhere
- Version without orginalcode:
Code:
alloc(newmem,2048)
label(returnhere)
label(exit)
00455D7F:
jmp newmem
nop
returnhere:
newmem:
add [ebx+0000030c],2
exit:
jmp returnhere
- Version with no use of newmem, just changing orginal code:
Code:
alloc(newmem,2048)
label(returnhere)
label(originalcode)
label(exit)
00455D7F:
jmp newmem
nop
returnhere:
newmem:
originalcode:
add [ebx+0000030c],2
exit:
jmp returnhere
For me every option worked, if you will have some error or something in any option, tell me.